Application Security Testing Services
Keep your applications secure with One Beyond’s Application Security Programme

When thinking of Security, several definitions come to mind. One of the simplest ways of viewing it is as the activities undertaken by an organisation or individual to protect a specific asset. This is still applicable in Cyber Security, although, as categoric as the above definition is, an asset cannot be either completely secure or not secure at all. There are always measures that can be taken into consideration to improve the “secure” state of one such asset and therefore we should think of it as a spectrum. Assets are more or less secure depending on the context they are in and the controls and vulnerabilities present in that context.
One Beyond offers an Application Security Programme, ensuring our applications, and others we maintain that were not necessarily developed by One Beyond, are as secure as they can be, based on a range of services. Any application developed by One Beyond will comprise of the following as standard:
- General best coding practices
- Secure coding practices
- Vulnerability scanning
- Basic penetration testing
As an optional upgrade to our standard service, we can also offer the following via our partnership:
- Threat modelling
- Static Application Security Testing (SAST)
- Software Composition Analysis (SCA)
- Dynamic Application Security Testing (DAST)
- Scheduled monthly Application Security Testing (SCA, SAST, DAST) and more in-depth Penetration testing
Why is Security important?
Cyber Security started getting more and more attention recently as stories about hackers damaging businesses are becoming commonplace. Based on extensive analysis, we can reveal:
- Hundreds of thousands of incidents happen every year
- Thousands result in successful breaches
- The majority are performed by highly skilled criminally associated hackers
- No industry, region or technology is spared
Now is the time to be taking Application Security Testing seriously, and One Beyond is here to assist you.
What does One Beyond’s Application Security Programme consist of?
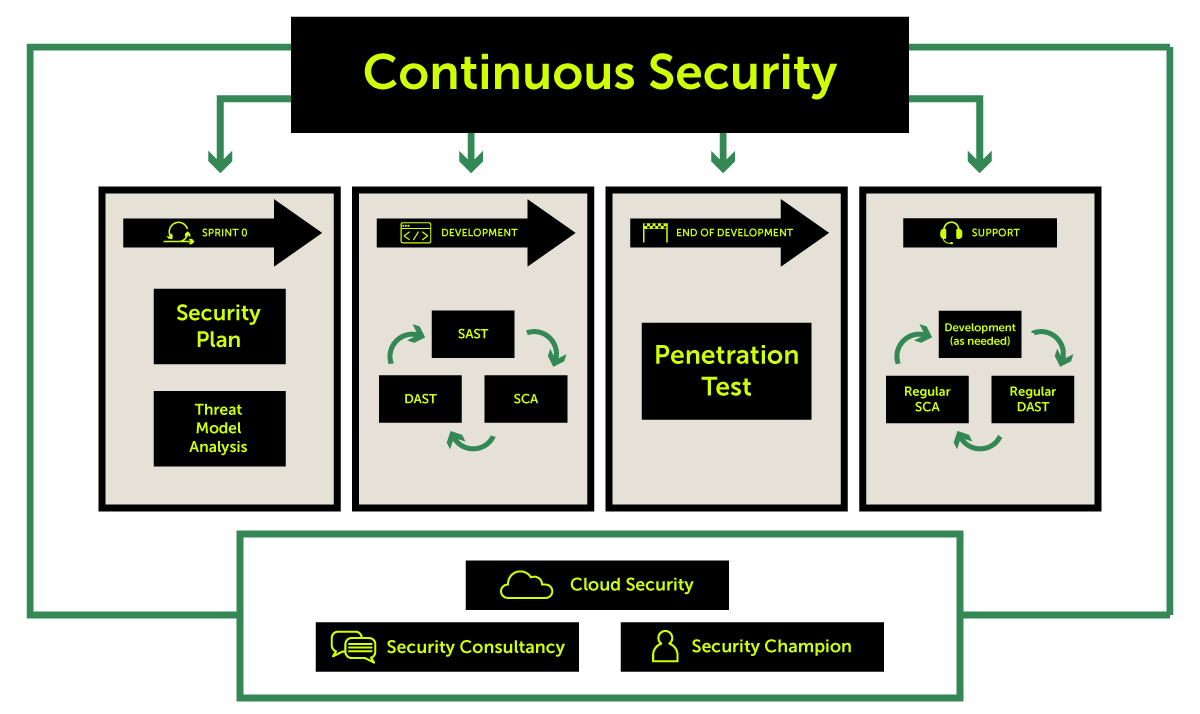
- In Sprint 0, Threat modelling is carried out to highlight any potential risk areas of the project from a security point of view to be taken into consideration in the final design and estimation.
- Once the project starts the Development phase, Static Application Security Testing (SAST), Software Composition Analysis (SCA) and Dynamic Application Security Testing (DAST) are performed regularly throughout the project, at a minimum of once per month.
- When Development has finished, Penetration Testing starts, taking into account all that has been discovered and remediated up to that point, scoping weak areas that are impossible to be found by automated testing, while complementing the areas which can, with further deep-dive testing.
- After the issues discovered during Penetration Testing have been remediated, the project enters in the Support phase during which SCA and DAST are performed regularly, at a minimum of once per month, with the option of performing SAST as well, if needed.
Our Application Security Programme can be adapted for your specific business requirements.
Further Information
What is Threat modelling?
The goal of threat modelling is to help you identify threats, attacks, vulnerabilities, and countermeasures that could affect your application, early on. We think the best place for this is as part of our Sprint 0, where the project is being defined. This way, one of our Security experts can analyse the Application to be and point out the features, areas or design decisions that would most likely result in vulnerabilities later down the line.
What is Software Composition Analysis? (SCA)
SCA is a process in which all open-source components and their dependencies are checked against a database of known packages with vulnerabilities and their versions. Keeping such a close eye on our collection of open-source packages is guaranteed to substantially reduce the risks of introducing vulnerabilities through open source packages.
What is Static Application Security Testing? (SAST)
Through this type of testing, the whole codebase of the project is being analysed with a state-of-the-art engine to detect possible issues with the code that can result in vulnerabilities.
What is Dynamic Application Security Testing? (DAST)
DAST is a type of application security testing that evaluates applications to see how they perform in the real world. While other forms of Application Security Testing can evaluate the quality of the code (SAST) and/or whether there are any known vulnerabilities in the third-party components (SCA) that our developers use, DAST scanning can check for configuration errors, certificate issues, deployment issues, as well as exploitable vulnerabilities instead of just flaws that may turn into a vulnerability.
What is Penetration Testing?
Penetration testing is a type of testing, that involves mostly manual approaches and tools, aimed at performing the same tasks as a real-life attacker would to identify hard to catch issues.